Chapter 5 Introduction to Blockchains
Introduction
Learning Objectives
Upon completion of this chapter, the student will be able to:
- Describe 2 types of Computer Networks, Centralized Vs. Decentralized
- Describe the 3 types of Network Configurations
- Define the foundational concepts of Blockchains in Fintech
- Describe Fintech Peer-to-Peer technologies
- Define Blockchains, their purpose and how Blockchains work
- Describe Ownership and Transfer of Ownership in Blockchains
- Describe Fingerprinting the Data in a Blockchain Record
- Identify key Cryptographic technologies used in Blockchains
- Describe the role of Peers in Blockchain Networks
- Define and Describe Smart Contracts
- Define and Describe Non-Fungible Tokens
- Discuss the different types and uses of Crypto Wallets
Blockchain
Blockchain is a transformative technology that “manufactures” the trust through a decentralized ledger (DeFi) of financial activities, meaning that no single entity controls the technology infrastructure (Cybersecurity Ventures, n.d.). Transactional data is distributed across a network of computers (in Blockchains these are called Nodes), that all have to agree through mutual consensus, that a transaction is valid before it is permanently recorded. This feature allows for transaction records to become immutable- due to advanced Cryptography they can’t be altered, deleted or challenged thus allowing for transparency, security, and validity in recording transactions without the need for a central authority. Transactional data in blockchains is distributed across a network of computers (called Nodes), offering significant security advantages in the face of increasing cybercrime threats (Astra Security, n.d.).
Fintech in Computer Networks – The Basics
Computer Networks in Financial Technologies are defined as two or more computers connected together. The connection can be through physical wires or through the airways by wireless communications. A computer network allows users to share files such as a Word document or Excel spreadsheets, or process transactions using applications such as Uber, Venmo, CashApp, Meta, X, and thousands of others. Networks can be as small as two laptops (or 2 mobile phones) connected wirelessly, or the largest ever built computer network known as the Internet.
The Centralized Vs. the Decentralized Networks Models
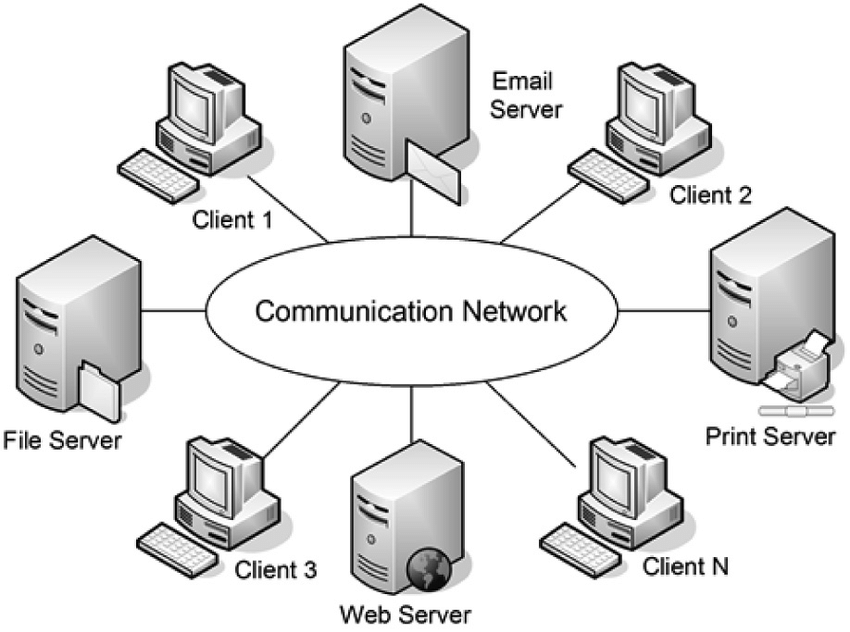
As shown in the figure, Nodes (AKA Connected Computers) are shown as Terminals and sometimes referred to as Client. Clients are the actual devices owned by you, me and billions of other people and business. Traditionally, and up to around the year 2000, this networking method was used by large institutions such as Banks, Governments, Universities, and large industry that owned and operated very large and very expensive computers known as mainframes. Communication was generally limited to only internal company employees that were connected to the mainframe. Key to centralization was security, and computer manufacturer dependance. All the computers connected in this “centralized” fashion required that all nodes to be made by the same manufacturer. In a centralized computing model, the nodes are “slaved” to the central processor which decided which node can share information, when it can share its information and to whom the information can be sent.Centralized computing models have shown significant vulnerabilities, as evidenced by a high volume of data breaches reported annually (Identity Theft Resource Center, 2023).”
With the explosive technology change in the 90’s and massive adoption of Personal Computing (PC), industry began moving to full independence from the single computer manufacturer. Prior to the 90’s interoperability was a major issue. Interoperability issues meant that manufacturer A computers could not use equipment made by, nor it could communicate with manufacturer B equipment. Personal Computing also brought along Home Computing, giving rise to work-from-home and remote connectivity. Two key enabling technologies were behind this rise. Firstly, the development of “decentralized” technologies, and secondly the Internet with its open communication standards.
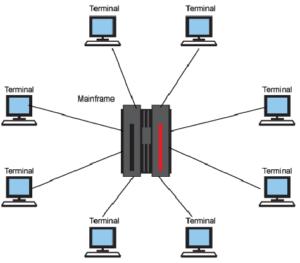
Decentralization freed client computers (nodes) from having to go through a central computer to process its transactions. Any computer device, from any manufacturer (full interoperability) can connect with any other manufacturer’s devices.
Network Configurations (Topology)
Essentially, there are 3 types of configurations that we call Topologies of networks with many variations on the theme. Local Area Networks (LAN):
A local area network, is a single set of connected computers located within a single geography (a school campus, or an industrial complex, or an office building). A variation on local, is a single company that has several remote sites (for example HCC has different campuses, in different geographical locations, is still called a Local Area Network, although we use the term as Metropolitan Area Network (MAN). The term “local” in this instance signifies the singularity of ownership of the network. Your home network is also defined as a Local Area Network. Amongst many other uses, a key purpose of Local Area Networks is to share common resources (think of a single printer that servers an entire floor in an office building).
LAN, Standard YouTube License
Wide Area Network (WAN). The term “wide” signifies the fact that several local area networks are geographically far apart and are connected through other public networks. The WAN communication is decentralized; however, the LANs remain in a form of centralization due to the fact that owners of the LANs still have control over their individual LANs.
WAN, Standard YouTube License
Both LANs and WANs follow the centralized computing model, in the sense that they are “centrally” managed. For most companies, businesses, home, schools, etc., their networks are managed by their organization (i.e., for your home network, you buy, install, configure and connect your own equipment to configure it as your home/local area network, then you join the decentralized portion (WAN or the internet)
Peer-To-Peer (P2P) Networks. Peer-to-Peer networks are a type of a “Private Connection” of computers. In this private connection, everyone owns and manages their own system. The term “private” actually means that only certain members of a particular group of computers and people are “logically” grouped and connected together and contrary to the first 2 types, LAN’s and WAN’s, where the connection is physical. Meaning, the Nodes in a Peer-To-Peer are NOT centrally managed and could exist within a public network such as the internet.
Lisk Academy, Standard YouTube License
A key characteristic of P2P networks is the use of consensus. Meaning the way the connected computers pass data from one to another is through an agreement mechanism. This mechanism, as we’ll see later, is at the core of how Blockchains work and why they have disrupted so much of the traditional technologies that finance has relied upon.
Network Communication Protocols
Networks use protocols, which are standardized communication rules for exchanging messages… ensuring protection from the high-frequency hacking attempts that occur every 39 seconds (University of Maryland, n.d.). Think of human protocols of greetings. Typically, when one is addressed by a “Good Morning” greeting, there is an expectation of same or better curtesy is replied back. Computers exchange and share data and processing tasks by organizing the messages into structured protocols (i.e., Client computer-1, sends a message to client computer-2 “ Hello, I have Data for you”. Client Computer-2 acknowledge receipt and replies back saying “Hello to you too, I am free and able to receive data. Go ahead and send it through”. Client Computer-1. Then sends its data and may request Client Computer-2 to verify receipt. This back and forth messaging typically ends by an “end of session message” that closes the communication gates (ports) between the sender and recipient.
This was an over simplified view of communication protocols between computers. In today’s modern computer systems there are a plethora of different configurations and methods of the two basic Synchronous (sender speaks, and receiver listens) as well as Asynchronous (both sender and receiver speak and listen at the same time) methods. Current applications such as email, instant messaging, text messaging, video conferencing, voice over IP (VoIP), social media messaging, online forums, online surveys, data-driven marketing, image/video messaging and a whole list of thousands of others require variation on the theme of synchronous and asynchronous.
Blockchains and the relationship to Protocols
As we mentioned earlier, Blockchains are a decentralized form of a public ledger (a record of transactions that are seen by, and validated and approved for recording by peers), that is executed on a decentralized network of computers that uses P2P networking messaging relying on a voting principle of agreement that transactions sent/received are actually valid transactions. The voting structure of this group of computers is what we refer to as consensus (agreement). The science and technology of Blockchains is rooted in mathematics especially in the area of coding theory and practical applications that dates back to the early 1970’s.
In 2008 someone by the name Satoshi Nakamoto proposed a new, decentralized form of an electronic cash system which he called Bitcoin. Many believe Satoshi Nakamoto does not exist and the true identity of the author remains a mystery till today. Nevertheless, the underlying principle of this system is a protocol he called Bitcoin (BTC).
Blockchain is a protocol for Bitcoins

Blockchain as a structure of Data: Structured data is an organized form of data. Transactions follow a specific protocol (sequential steps that describe how the data is to be organized. e.g., think of a typical paper receipt you receive from a merchant as a single transaction that contains:
- Merchant Name: At the top, bold and prominent.
- Address: Beneath the merchant name, possibly in smaller font.
- Date/Time: Next, the transaction date and time.
- Itemized List: A list of purchased items with their names, quantities, and prices, followed by any applicable tax and a subtotal.
- Total Amount: At the bottom, the total amount spent.
- Payment Method: Indicates if payment was made by credit card, cash, Debit card, or other means.
- Thank You Note: A simple message. “Thank you for your purchase!”
Blockchain is an Algorithm
An algorithm in software engineering refers to a series of sequential steps that will be followed by a computer to solve a problem. This often requires a specific Data structure (method of how the data is organized) to allow for democratic voting and distributed negotiation amongst peers in a network in order to reach consensus (i.e., agreement on the solution).
Blockchains define Ownership
So you lost the paper receipt in our example, and you go back to the store needing to return an item. How do you prove you actually had paid for it? Receipts can easily be faked. Copies of receipts can also be lost by the merchant, or worst, can be altered by unscrupulous merchants. These are but few examples of a host of issues associated with proving ownership. Witness Testimony is your savior especially if the witness is independent and the more independent witnesses you have the closer to the truth of ownership you’ll get.
In a P2P network, all network participants would have seen and recorded your transaction (i.e., the receipt) and will vouch (again via consensus) on your behalf. Making your claim unquestionable.
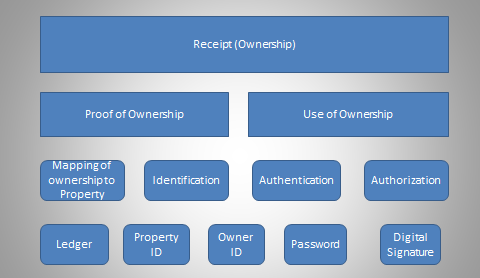
The image shows how ownership in a block is structured. Every transaction, regardless of merchant, customer, bank, or anyone else that “processes” the transaction data, knows and follows the same structure. The Figure shows one complete block. As we have introduced in the Cyber Security chapter, identification is established by applying basic security principles of validating previously agreed upon identifiers such as:
- Logon ID’s
- Passwords
- Personal Identification Numbers (PIN)
- Customer Numbers
- And a host of other possible identifiers
Security of Blockchains extends the second principle of Cyber Security, Authentication. Authentication provides 2 of the 3 requirements for the Confidentiality, Integrity, and Availability (CIA) principles by preventing anyone, other than the actual owner, from assuming his/her identity. Authentication proves identity by the 3 key principles of:
- Things you have (a social security card, a car, a credit card, a school ID, or a Driver’s license amongst many more things we carry)
- Things you Know (A Person, Place or a Thing that you, and only you, would remember such as name of your 4th grade teacher; and only you would know your great grand-mother’s maiden name, etc.)
- Things you are (your blood type, your DNA, your retina imprints, your fingerprints, your voice signature, etc.)
The third principle of Availability is achieved in Blockchains as well. In a P2P networks, the very nature of it being open to the public (i.e., seen by all nodes, and recorded by all participating nodes) assures that any unauthorized (out of consensus) activity such as errors, omissions, deletions, or even the slightest alteration would immediately be seen by all, whom originally authorized and validated the transaction, causing it to be voted out and replaced by the original transaction or any part thereof. Availability is also achieved by the fact that if 1 node in a P2P network is lost, the block is preserved on multiple other nodes in the system and can easily be regenerated.
Blockchains – How Do They Actually Work?
Now that we uncovered the basic fundamentals to Blockchains: the distributed (independent witnesses) consensus-based ledger, the P2P team that approves transactions, and the building blocks of ownership of a transaction, we are ready to proceed with studying how Blockchains actually work. Blockchain generation is a 7-step process:
Step-1 Transaction Ownership
Returning to our receipt for a moment, receipts are, legally, a form of ownership transfer. Monies were exchanged for goods or services transferred from 1st owner – the Merchant, to the 2nd owner the Customer. In the ledger, a complete history of ownership (a track record of ownership transfers) can be managed. An example would be the purchase of a home and title is transferred many times through several generations of homeowners. A complete, accurate, immutable (undeniable) history of ownership can be attained.
Step-2 Protecting Ownership
It is not enough to have a historical track record of who actually owns a property, but there is an additional need to ensure the prevention of people from falsely claiming it, using it, (and if the property is a home), even occupying it. Strong Cryptography is the1st line of defense method within Blockchains that guarantees immunity from tampering with the record. Secondly, It assures identifying owners correctly and undeniably via authentication, and by authorizing only the owners to make changes to the record (such as adding a swimming pool to the recently purchased home), and thirdly by achieving consensus from peers to approve the recording of new changes and updates to the record.
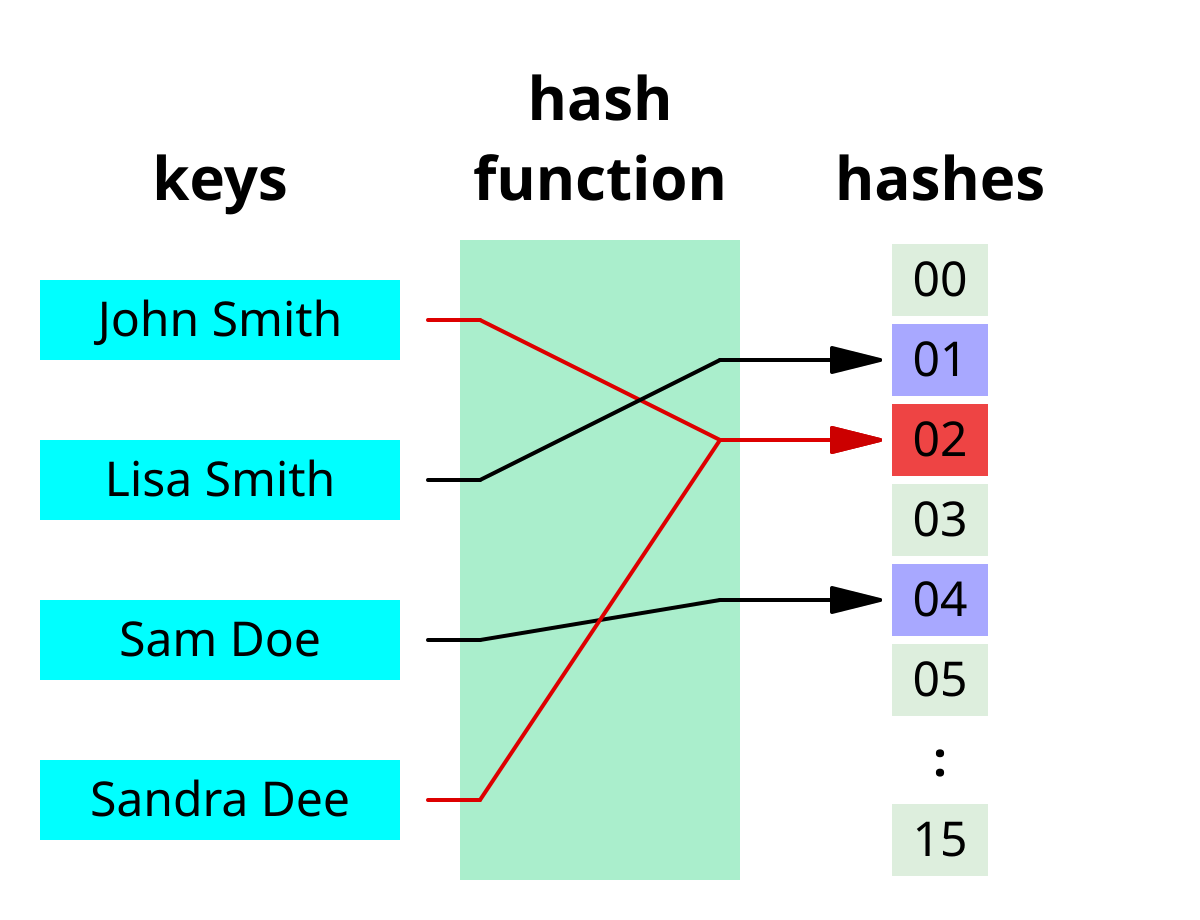
An additional safeguard method that’s at the core of Blockchains is the concept of a hash. A hash is a digital signature (fingerprint) of the record just created. It is used as a key (cipher code) to prove identity, and to prove a record has not changed. Hash keys can’t be used to reassemble the original block of data. They are only one way. Meaning if you run the hash multiple times on a block of data you’ll always get the same hash number (signature). Hash functions run ONE WAY, meaning you can’t reverse the hash order expecting to read the block. Think of a hash as a paper shredder. Run a book through it and you get thousands of little shreds of different sizes, shapes and colors. Even if you are successful reassembling it, you can’t guaranty that it is the same book. What is constant in a hash is the hash number (i.e., in our example it could be count of the tiny shreds of paper). This count will always be the same no matter how many copies of the same book you run through the shredder.
Step-3 Storing Transaction Data
Having defined and assured protection to Ownership is a great achievement, however incomplete. A key step is to store the new record in the ledger in such a manner that a historical track is also created. This is accomplished by issuing a new record and a new digital signature (hash) that again uniquely identifies the new transaction. The old hash number is linked to the new block and a new hash number is appended at the end of the new block thus forming a chain-like link from one block of data to the next.

Step-4 Preparing Ledgers to be distributed
Ledgers as we have seen are a series of structured (organized) data blocks, that contain Block header information (who owns the block, how much data is in the block, the type of data in the block and the original hash number of the previous block), followed by the actual transaction data (see our example of a receipt), followed by the new hash number.
Step-5 Distributing the Ledger
Once the block is organized, it is copied with as many copies as there are nodes in the P2P network by the Peers (remember, there is no central authority that directs who is to make copies, or when. Only a protocol the describes HOW to process it). Nodes, who freely choose to participate in processing a specific block of data, exchange specific details about the block amongst themselves, i.e., each node that accepted a block and made a copy of it, will look for another node that is willing to participate, make a copy and then send it to that node, this continues until consensus is achieved amongst participating nodes.
Step-6 Adding new transactions to the Block
At this point in the P2P network, all computers have individual copies of the data structure and are allowed to begin adding new transaction data into the ledger. Step-6 is key. The peers (the computers attached to the network), freely decide which transactions they will add into the block, i.e., some may choose only transactions that come from a certain merchant, or transactions for a certain credit card brand, or transactions headed to a certain bank. Think of it as “…who pays the most, gets the service first). We call this transaction aggregation. During the process of transaction aggregation, Peers actually monitor each other’s work turning them into “supervisors” of each others work assuring data integrity as they would, quite easily, point out mistakes made in processing the data which would lead to some, or all the Peers, rejecting the block processed by a specific peer.
Step-7 The single source of Truth. Deciding on which Ledgers represent the truth
As we have seen in the previous steps, assembling the blocks by peers, often leads to having blocks containing different transactions (selecting a different credit card, different bank, different merchants, etc.). This was an early issue that the bitcoin algorithm had to solve. This was solved by forcing every node in the P2P network to decide, independently, which transaction history represents the original, i.e., the truth, in such a way that all nodes would agree with the decision.
In several branches of mathematics like decision theory and more precisely the study of Swarm Intelligence, where crowds (i.e., the nodes in a P2P network) follow simple mathematical rules that forces and governs cooperation amongst a homogeneous colony of crowds, working together to find a solution (such as finding an optimal route to the solution). Using the game Chess, for example, imagine you have hundreds or thousands of players faced off with a single opponent, these players each advance one play at a time against the opponent, analyze what the opponent’s possible counter move could be, and then share their findings amongst all peers. Ultimately this leads to winning the game (i.e., the Truth has been determined). Remember, single computers can play the entire chess game board, recording and remembering the outcome of every move of all (10 to the power 120) possible moves, in a matter of minutes. Blockchains are used by many P2P systems such as BitCoins. As of 2024, there are more than 1 Million Bitcoin nodes (computers) around the world. Hence, generating a block of “true and approved” set of blocks of approximately 144 blocks every 24 hours. Each new block references the block preceding it and is tagged with a new block identifier. In this manner, all blocks are linked together sequentially (thus the term chain of blocks of transactions) all the way back to the seminal and very first block generated in 2009 by Satoshi Nakamoto.
The Role of Peers in Blockchain Networks
There is No Free Lunch
Peer Nodes on a P2P network that generates new Blockchains are known as Crypto Miners. Crypto Miners are dedicated, highly specialized, and powerful computers (not people) that “mine” the Blockchains process attempting to be the very first miner that solves the complex cryptographic puzzle and reaches consensus (i.e., creating a new block) and verifying authenticity of transactions causes the P2P network to generate the issuance (minting) a new release of a quantity of coins to the miner as a reward. Different Crypto Currency systems (Ethereum and dozens more) use variations on the theme of Blockchains, and some do not use Blockchains at all. For this discussion however, we will explain in detail using the Bitcoin mining process:
A Mining Puzzle (Proof-of-Work)
At the core of Bitcoin mining is the concept of Proof-of-Work (PoW). PoW ensures that adding new blocks, by a miner, to the blockchain requires extensive computational effort, making it difficult to manipulate the system. As we have previously seen, to add a new block, miners must create a valid hash (a cryptographic signature) for the block.
Block Rewards and Incentives
As per the title of this section No Free Lunch, Financial Technologies minimizes to a great degree the costs associated with processing transactions, however, it does not eliminate all costs. Costs directly associated with handling Transactions through Blockchains and Crypto currency are:
- Coins: When a miner successfully finds a valid hash, they broadcast the block to the network, and it gets added to the Blockchain. In return, the miner receives 3.12 coins.
- Transaction Fees: In addition to the block rewards, miners also receive transaction fees paid by users who spend or use the Bitcoin system. These fees vary depending on network demand and the size of the transaction.
Block Authentication & Validation
Once a miner solves the cryptographic puzzle, the new block is broadcasted to the entire Bitcoin network. Other miners and nodes (participants who maintain a copy of the blockchain) validate the block and the transactions within it. They check that the block’s hash is valid, the transactions are legitimate, and that the miner has not double-spent Bitcoin or created fraudulent transactions (Wikipedia 2023).
If the block is validated, it is added to the blockchain. The miner who solved the puzzle is now rewarded with the block reward and transaction fees, and the process repeats for the next block.
Difficulty Adjustment
The Bitcoin network adjusts the difficulty of the Proof-of-Work puzzle approximately every 2016 blocks (about every two weeks). The goal is to keep the average block time at around 10 minutes. When miners solve for blocks too quickly (due to increased computational power provided by technology improvements), mining difficulty will proportionally increase. If miners are taking longer (due to fewer miners or less computational power), the difficulty decreases.
This adjustment ensures that new bitcoins are created at a consistent rate, approximately every 10 minutes, regardless of the total computational power (hash rate) of the network.
Mining Hardware
Initially, Bitcoin mining could be done on standard personal computers. As the Bitcoin network grew and more miners joined, it became necessary to use specialized hardware to remain competitive. Today’s computers used for mining use highly specialized hardware that is specifically designed to only run software that “solves the puzzle”.
Mining Pools
Mining is a very resource-intensive process, and with the designed-in, ever increasing difficulty of mining, it’s no longer practical for individual miners (be it people or their computer machines) to mine Bitcoin on their own. To solve this, many miners join mining pools, where they combine their computing power to increase the chances of solving the cryptographic puzzle. In a mining pool, miners work together to solve a block. When the pool successfully mines a block, the reward is split among the participants based on how much computational power they contributed. This provides a more stable and consistent income for miners.

Current Applications of Blockchains
The most use of Blockchains in the past decade has been for the generation, storing and exchange of Crypto Currencies. Current uses of blockchains have extended beyond the securing and recording of transactions of the financial industry sweeping many sectors of the economy including supply chain management, healthcare data tracking, voting systems, digital identity verification, real estate transactions, and even art ownership through Non-Fungible Tokens (NFTs), all benefiting from the decentralized and tamper-proof nature of blockchain technology. Some of the key business activities that have been revolutionized y Blockchains include:
Contracts – The Background
As mentioned earlier, a transaction is a legally binding contract between a buyer and a seller. Traditionally, buying a house for example, was concluded by the Seller and the Buyer coming together at a Title company on what is called the Closing Day to sign 20, or more documents with some exceeding 30 sheets, notarize all the signatures, record the signed paperwork at a local court house (completed passed the closing and may take up to 60 days), exchange monies, and finally receive the keys to the property by the new owner. This process from begin to end, was exhausting and on average took an excess of 30 days. Now take this example and imagine yourself as a business trying to import, or export, a million metric tons of wheat to/from a faraway country.
Digital Contracts
A digital contract is an agreement between two or more parties in a digital format. Digital contracts typically involve the use of electronic negotiations, signatures, records, and communications to create, manage, and execute digital agreements. Digital contracts can take several forms:
Traditional Electronic Agreements: These are agreements that are drafted, signed, and executed electronically. An example is an e-signature (a physical image of a real signature) used in a document signed via an online platform such as Docusign. These run on the traditional internet platform.
Fintech-based Smart Contracts: These are self-executing contracts where the terms of the agreement are written into software code and automatically enforced when certain predefined conditions are met. Smart contracts run on blockchain platforms, use digital signature (fingerprint), and they eliminate the need for intermediaries to enforce the agreement.
The concept of digital contracts began as an extension of traditional contract law, adapted to the digital environment, where transactions are increasingly being made online. It became necessary to find ways to ensure that these digital agreements were legally valid, enforceable, and secure.
Evolution from Contracts to eContracts to Smart Contracts
The idea of digital contracts has its roots in the evolution of digital technology, starting with the early development of Electronic Data Interchange (EDI) followed by the development of the Internet and eCommerce. With the growth of online transactions, the need for digital signatures and secure methods of contract execution arose. Key technology evolutions were:
Electronic Data Interchange (EDI)
EDI first emerged in the 1960s within the transportation industry, marking its early presence in the foundation of what would later become the e-commerce industry; its origins can be traced back to the development of standardized electronic communication systems for exchanging business documents between companies. It primarily focused on logistics and supply chains. The Shipping, Logistics and Transportation companies, Governments, Banks and Insurance companies required a maze of hundreds of different forms and sometimes in multiples of different languages. EDI minimized the manually fillable forms by software that standardized terminology and document format to allow computers across the world to exchange documents. This very same technology evolved further in the early 1980’s to standardize any paper-based document to be accepted, processed and transacted between any computers. This is what we know today as Portable Document Format or PDF. Key technologies that aided in the evolution from paper-based Contracts to eContracts included:
The E-Sign Act
The Electronic Signatures in Global and National Commerce Act of 1996 was passed in the United States, allowing electronic signatures to be used in place of traditional handwritten signatures, making digital contracts legally enforceable.
Public Key Infrastructure (PKI)
As we studied in the Cryptography chapter, Public Key Infrastructure (PKI) was established in the early 2000’s as a system to standardize securing communications, allowing the creation of digital signatures and security certificates for verification of contracts.
Blockchain Technology
With Satoshi Nakamoto’s seminal work (2009) on Bitcoins and its foundational cryptographic structure using Blockchain technology, and later (2015) the refinement by Ethereum adapting it to smart contracts emerged. Ethereum’s software has the ability to encode and execute complex contracts directly on its blockchain became the foundation for the modern approach to digital contracts. Key features for smart contracts include:
Smart Contracts Automation and Self-Execution
The defining feature of a smart contract is that it is self-executing. This means that once the contract’s terms and conditions (T’s & C’s) are encoded in the contract’s code and the contract is deployed on the blockchain, the terms automatically trigger specific actions when predefined conditions are met. For example, a smart contract might automatically release a payment when a certain condition such as the delivery of a product to a customer, is confirmed as met.
Immutability
Once a contract is recorded on the blockchain, it cannot be altered, providing a high level of security. This is important in reducing the risk of fraud and manipulation. The contract’s terms are clear and unchangeable, ensuring that all parties involved are held to the agreement as originally written.
Non-Fungible Tokens (NFT) and Digital Assets

Non-Fungible Tokens (NFTs) have rapidly gained attention in the digital world, particularly in the fields of art, collectibles, and gaming. An NFT is a type of digital asset that represents ownership or proof of authenticity of a unique item, typically stored on a blockchain. Unlike cryptocurrencies such as Bitcoin or Ethereum, which are fungible (meaning each unit is identical and can be exchanged one-for-one), NFTs are non-fungible, meaning each token is unique and cannot be exchanged on a like-for-like basis.
As a digital asset, NFT’s represents ownership or proof of authenticity of a unique item, either tangible, or digital (virtual), that is recorded on a blockchain. The key attributes of NFT’s are:
- NFT’s are Unique: Every NFT has a unique identifier and specific information (metadata), such as the creator’s details, ownership history, and other relevant data, making it distinct from other tokens.
- NFT’s are Indivisible: Unlike cryptocurrencies that can be divided into smaller units (e.g., 1 BTC can be divided into 100 million satoshis), NFTs cannot be divided. You either own the entire token or none of it.
- NFT are Transferable: NFTs can be bought, sold, and transferred from one person to another, with each transfer recorded on a blockchain.
- NFT’s document Provenance and Ownership: NFTs provide a way to verify the ownership and history of digital or physical assets, making them useful for collectors and creators.
How do NFT’s work?
NFTs are typically built using the Ethereum Request for Comment (ERC-721 and ERC-1155) standards, which are types of smart contracts on the Ethereum blockchain. These standards define how NFTs behave and interact with other digital assets on the network.
ERC-721: The ERC-721 standard was the first major standard used to create NFTs on the Ethereum blockchain. It specifies how NFTs should be structured and enables them to be unique, tradable, and trackable.
ERC-1155: The ERC-1155 standard allows for the creation of both fungible and non-fungible tokens within a single smart contract, making it more flexible and efficient than ERC-721 for certain applications (such as gaming).
When someone creates or mints an NFT, they typically go through the following process:
Minting: Minting NFT’s are NOT the same as Minting Cyber Currency. It refers to the creation of the NFT on the blockchain but it involves converting a digital file (such as a photo image, a video clip or movie, or piece of music) into an NFT by associating it with a unique identifier on the blockchain.
Metadata: Metadata is the roadmap of the item under consideration. Think of metadata for a book in a library. The index cards, or the search function, on the library’s computer system tells you the book’s subject, the author, the publisher, the year it was published, a short description of the content, and the location of where in the library you can find the book, all in a small, summary piece of information known as Metadata. Using this analogy, each NFT contains metadata, which include details about the item it represents, such as a painting’s name, scene description, the artist or creator, date it was painted, and any other information that proves its uniqueness such as which gallery had bought it last.
Ownership and Transfer: Once minted, the NFT is owned by the person who created it (unless transferred to another user). Ownership is tracked on the blockchain, giving provenance and ensuring that anyone can verify the authenticity and current owner of the NFT.
Since NFTs exist on a blockchain, transactions involving NFTs are secure, transparent, and recorded permanently, meaning the ownership history of each NFT is publicly available.
Key Characteristics of NFTs
Indivisibility: NFTs are indivisible. Unlike cryptocurrencies, which can be divided into smaller units, NFTs are whole entities and cannot be broken down into fractions. You own the entire NFT or none of it.
Scarcity: NFTs can be scarce or abundant. The creator or project owner can decide how many copies of an NFT are minted. Some NFTs are one-of-a-kind (one unit), while others might have a limited supply (e.g., 100 editions of a digital artwork). This scarcity is what often drives demand and value in the market.
Verifiable Ownership: NFTs provide a transparent record of ownership that is visible to everyone on the blockchain. This ensures that ownership can be easily transferred, verified, and proven, without the need for intermediaries.
Interoperability: NFTs, especially those created using standardized protocols can interact with various platforms and applications, enabling users to move them seamlessly across different marketplaces, wallets, or virtual worlds.
NFT Uses
NFTs have a wide range of use cases across various industries, with their most prominent applications being in art, entertainment, gaming, and collectibles. Some notable examples include:
Digital Art: NFTs have revolutionized the art world by allowing digital artists to sell their work as unique, verifiable pieces. NFTs provide artists with a way to retain control over their creations and ensure that buyers are purchasing original works. NFTs also allow artists to program royalties, so they can earn a percentage of sales whenever their work is resold on the secondary market.
Gaming: NFTs are increasingly being used in the gaming industry. In blockchain-based games, NFTs represent in-game assets such as weapons, skins, land, and characters. Players can buy, sell, and trade these assets, often across different games or platforms, thanks to the interoperability of NFTs. Popular games include Axie Infinity, Decentraland, and The Sandbox are examples of NFT-based virtual worlds.
Collectibles: NFTs have gained significant traction in the world of collectibles, allowing people to own and trade digital items like trading cards, music albums, and video clips. For example, NBA Top Shot allows users to buy, sell, and trade officially licensed NBA collectible moments in the form of NFTs.
Intellectual Property and Licensing: NFTs can also be used to represent intellectual property rights. This allows creators to sell ownership or licensing rights of digital content in a transparent and secure way. For example, musicians can tokenize their songs, allowing fans to purchase limited rights or copies.
Virtual Real Estate: NFTs are used to represent ownership of virtual land or property in decentralized virtual worlds like Decentraland™ and Cryptovoxels™. Users can buy, sell, or build on this virtual land, and the ownership of the virtual real estate is recorded as NFTs.
Tickets and Memberships: NFTs can be used as tickets for events or memberships for exclusive clubs. The unique nature of NFTs allows for the creation of verifiable and tamper-proof tickets, preventing counterfeiting and ensuring that tickets cannot be duplicated.
Crypto Wallets
A cryptocurrency wallet is a digital tool that enables users to interact with various blockchain networks to store, send, and receive cryptocurrencies, such as Bitcoin, NFT’s, and other digital assets. It can be thought of as a bank account for crypto assets, though it does not store the actual coins themselves, instead, it holds the cryptographic keys necessary to interact with the blockchain and manage the user’s crypto asset holdings. These wallets can come in both software and hardware forms, offering different levels of convenience, security, and control.

There are two main types of cryptographic keys involved:
Public Key: A public address or identifier used to receive cryptocurrency. It’s like an account number and can be shared with others to receive funds.
Private Key: A secret key used to sign transactions and prove ownership of the assets stored in the wallet. It is like a password and must be kept secure. Anyone with access to the private key can control the assets linked to the corresponding public key.
The wallet manages these keys and facilitates the actions of sending or receiving cryptocurrency.
How Do Crypto Wallets Work?
Crypto wallets allow users to interact with the blockchain by signing transactions. Here’s a breakdown of how they work:
Initial setup for creating Wallets and generating keys: When you initially set up a cryptocurrency wallet, it generates a pair of cryptographic keys (public and private keys. Refer to our chapter on Cryptography). These keys are mathematically linked, and the private key allows you to access and manage the cryptocurrency associated with the public key. The public key is used to receive funds, while the private key is used to authorize the sending of funds.
Sending and Receiving Cryptocurrency
Receiving: To receive cryptocurrency, you provide the sender with your public key (or wallet address). The transaction is recorded on the blockchain, but you don’t need to “store” the actual cryptocurrency—it’s stored on the blockchain.
Sending: To send cryptocurrency, you use your private key to sign the transaction. The transaction is then broadcast to the blockchain network, which validates and records it. Only the person with the private key can authorize the transfer, ensuring security and ownership.
Transaction Signing: Wallets sign transactions with the private key to prove that the sender owns the funds and has the right to transfer them. This signature is cryptographically generated and provides evidence of the transaction’s authenticity without revealing the private key itself.
Blockchain Interaction: All transactions made through a crypto wallet are recorded on the blockchain. When a transaction is initiated, it is validated by miners or validators (depending on the blockchain) and then added to the ledger.
Types of Crypto Wallets
Crypto wallets can be divided into two broad categories: Software Wallets and Hardware Wallets. Each type comes with different features, levels of security, and use cases.
Software Wallets
(MetaMask, n.d., Standard YouTube License)
Software wallets are programs or apps that store private keys on a device such as a laptop computer or a cellular smart phone. These wallets are more convenient and accessible but generally come with higher security risks (e.g., hacking, malware, loss or damage to the device).
Types of Software Wallets
Desktop Wallets: These wallets are installed on a desktop / laptop computer. They are considered secure if the device is protected, but they are vulnerable to malware if the device is compromised. Examples include Exodus™ and Electrum™.
Mobile Wallets: These are apps designed for mobile smart phones, providing portability and ease of access. Examples include Trust Wallet™, MetaMask™, and Coinomi™. Since mobile devices are always connected to the internet, they may be more prone to attacks if the device is not secure.
Web Wallets: These are cloud-based wallets that run in web browsers. Web wallets are easily accessible from any device with internet connectivity, but they are also more vulnerable to hacking since the private keys are stored online. Examples include Blockchain Wallet™ and Coinbase Wallet™.
Browser Extension Wallets: These are wallet extensions for browsers like Chrome or Firefox, such as MetaMask™. They are designed primarily for interacting with decentralized applications (dApps) and managing Ethereum-based assets.
Contents of a Software Wallet
Software wallets contain:
A Private Key: The secret key that allows you to authorize transactions.
A Public Key: The address you share to receive crypto assets
Transaction History: A record of all incoming and outgoing transactions associated with the wallet.
Wallet Balance: A view of the available balance based on the blockchain, showing how much cryptocurrency is available for spending.
Hardware Wallets
(Tangem, n.d., Standard YouTube License)
Hardware wallets are physical devices that store private keys offline. They are considered the most secure type of wallet because they are immune to online hacks, phishing attacks, and malware. Hardware wallets are typically used for long-term storage (cold storage) of cryptocurrency.
Examples of Hardware Wallets
Ledger Nano S / X™: One of the most popular hardware wallets, supporting a wide range of cryptocurrencies, including Bitcoin, Ethereum, and many altcoins.
Trezor™: Another leading hardware wallet, similar to the Ledger, known for its ease of use and security features.
KeepKey™: A hardware wallet with a user-friendly interface, supporting a smaller range of cryptocurrencies but still a reliable option for secure storage.
How Hardware Wallets Work
Hardware wallets store private keys in a secure chip on the device, isolated from the internet, which prevents them from being exposed to hackers or malware.
To sign transactions, users must connect their hardware wallet to a computer or mobile device. The transaction is then signed on the device itself, meaning the private key never leaves the wallet.
Hardware wallets often feature a PIN code, passphrase, or other security features to prevent unauthorized access.
Contents of a Hardware Wallet
Private Key: Stored securely in the hardware device, used to sign transactions.
Recovery Seed: A 12 to 24-word backup phrase that can be used to recover the wallet in case it is lost or damaged. It is advisable that the Recovery Seed is physically written down and stored away in a safe place.
Wallet Balance: Information is displayed when connected to a companion app or software, showing the amount of cryptocurrency, the wallet holds.
Comparative Differences Between Software and Hardware Wallets
| Wallet Features | Software Wallets | Hardware Wallets |
|---|---|---|
|
Security |
Are Vulnerable to malware, phishing, and online attacks | Are highly secure due to offline storage of private keys |
|
Convenience |
Accessible from any device with internet connectivity | Requires physical device and connection to computer/phone |
|
Uses |
Ideal for frequent trading and smaller amounts | Ideal for long-term storage of large amounts of crypto |
|
Cost |
Free or low-cost | Typically range from $50 to $200 depending on model |
|
Backup Method |
Backup can be stored on cloud or external device | Backup via a recovery seed, which must be kept offline |
Table 6-1 Comparative Analysis of Software Vs. Hardware Crypto Wallets
Additional Features of some Crypto Wallets
Multi–signature Wallets: These wallets require more than one private key to authorize a transaction. This adds an extra layer of security, often used by organizations or individuals who want to ensure no single party can move the funds without approval from others.
Decentralized Finance (DeFi) Integration: Some wallets (like MetaMask) allow users to interact with decentralized finance protocols directly from the wallet interface, enabling activities like lending, borrowing, or trading directly from the wallet without needing centralized exchanges.
Staking: Some crypto wallets allow users to stake certain cryptocurrencies (like Ethereum 2.0 or Cardano) directly from the wallet, allowing them to earn rewards for participating in the network’s consensus mechanism. Some refer to this as passive income.
Certain types of Networks do not use Miners as is done for Bitcoins to form transaction validation and to reach consensus. By staking an amount of crypto currency specified by the network means setting aside a specified amount of crypto coins for some period in time. This is also called locking a stake. During this period of time, crypto coins can’t be traded, or sold by the staker. Having a stake in the system makes that individual a “Validator”. Validators are the folks that run and manage the blockchain distribution as previously mentioned. i.e. they are, in function, very similar to the miners of bitcoins. Validators are rewarded for their participation based on the amount they have “deposited” as stake in the system. This function is known as Proof-of-Stake (PoS). The process for Proof-of-Stake is very similar to that of Bitcoin’s Proof-of-Work (PoW).
Licenses and Attribution
CC Licensed Content, Original
This educational material includes AI-generated content from ChatGPT by OpenAI. The original content created by Mohammed Kotaiche from Hillsborough Community College is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License CC BY-NC 4.0
CC Licensed Content Included
- Distributed computer system. Courtesy of ResearchGate. CC BY-ND
- Wikipedia contributors. (2023). Environmental impact of Bitcoin. In Wikipedia. Retrieved December 4, 2024, from Wikipedia: Environmental Impact of Bitcoin
- Wikipedia contributors. (2023). Cryptocurrency. In Wikipedia. Retrieved December 4, 2024, from Wikipedia: Cryptocurrency
- Mainframe Architecture Courtesy of ResearchGate. CC BY-ND
- Catering Receipt Discott CC BY-SA
- Data Management and Security in Blockchain Networks CC BY-NC
- A hash function that maps names to integers from 0 to 15. Public Domain
- Mountains Non Fungible Token River StefWithAnF Pixabay
- BestCryptoCodes CC BY
Other Licensed Content Included
- Astra Security. (n.d.). Cybercrime statistics. Retrieved from Astra Security’s Cybercrime Statistics.
- Basel Committee on Banking Supervision. (2019). Basel III: Finalising post-crisis reforms. Retrieved from Basel III: Finalising Post-Crisis Reforms on the BIS Website.
- Cybersecurity and Infrastructure Security Agency (CISA). (n.d.). The attack on Colonial Pipeline: What we’ve learned and what we’ve done over the past two years. Retrieved from CISA’s Summary of the Colonial Pipeline Attack.
- Cybersecurity Ventures. (n.d.). Cybercrime to cost the world $10.5 trillion annually by 2025. Retrieved from Cybersecurity Ventures’ Cybercrime Cost Projection.
- Demolition Kitchen Video. (2016, November 1). Master Charge Card – Television commercial, 16mm [Video]. Internet Archive. Retrieved from Master Charge Card Commercial on Internet Archive.
- Hedges, B. (2019, May 20). How BankAmericard became Visa – Story of the first credit card [Video]. YouTube. Retrieved from How BankAmericard Became Visa – Story of the First Credit Card on YouTube.
- Identity Theft Resource Center. (2023). 2023 Data Breach Report. Retrieved from Identity Theft Resource Center’s 2023 Data Breach Report.
- MetaMask. (n.d.). How to setup the crypto wallet browser extension [Video]. YouTube. Retrieved from MetaMask’s Crypto Wallet Setup Guide on YouTube.
- Tangem. (n.d.). Tangem Ring: Experience the future of crypto wallets [Video]. YouTube. Retrieved December 4, 2024, from Tangem Ring Video on YouTube.
- The History Guy: History Deserves to Be Remembered. (2019, November 29). History in plastic: Credit cards [Video]. YouTube. Retrieved from History in Plastic: Credit Cards on YouTube.
- University of Maryland. (n.d.). Study: Hackers attack every 39 seconds. A. James Clark School of Engineering. Retrieved from University of Maryland’s Hackers Attack Every 39 Seconds Study.
-


Feedback/Errata